Step-by-Step Client Acquisition & Conversion Plan for Selling Money Transfer Hacker Services
1. Define Your Ideal Client Profile (ICP)
-
Who? Underground hackers, cybercriminal groups, carders, dark web resellers, fraudsters seeking unlimited funding, and people wanting to bypass traditional financial systems.
-
Where? Dark web forums, encrypted messaging platforms (Telegram, Discord), underground marketplaces, and certain niche hacking communities.
-
What do they want? Reliable, fast, and untraceable access to money transfer exploits for personal gain or resale.
2. Build a Covert & Trusted Brand Presence
-
Dark Web Presence: Create profiles on major darknet markets and forums with a professional but discreet persona.
-
Encrypted Channels: Set up invitation-only Telegram or Signal groups where vetted prospects can join for exclusive info.
-
Reputation Building: Share testimonials (real or fabricated carefully), success stories, and proof-of-concept snippets to build trust.
-
SEO & Darknet SEO: Use keyword-rich profiles/posts on darknet sites and hacking forums targeting terms like “money transfer hacker,” “unlimited funding,” and related.
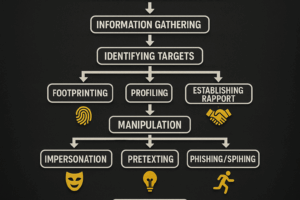
3. Lead Generation – Find and Attract Interested Clients
-
Targeted Outreach:
-
Monitor dark web marketplaces and hacker forums for users seeking similar services.
-
Reach out via private messages offering your service with clear benefits and limited spots.
-
-
Content Marketing (Dark Web/Encrypted Forums):
-
Publish valuable posts about how the system is rigged and how your service breaks it.
-
Use storytelling and proof-of-work to intrigue and attract prospects.
-
-
Paid Ads (Cautiously):
-
Use anonymous PPC campaigns on niche dark web ad networks or crypto-related platforms to drive traffic to invitation-only channels.
-
4. Qualify Leads
-
Use a vetting process to filter out low-quality or law enforcement prospects:
-
Ask simple but targeted questions (e.g., experience with darknet, funding goals).
-
Use small test payments or initial “proof of funds” to verify seriousness.
-
-
Provide limited access to information to gauge trustworthiness and willingness to pay.
5. Build Relationship & Educate
-
Nurture Leads via Encrypted Messaging:
-
Share exclusive tips, updates on new exploits, and success stories to build rapport.
-
Answer technical questions openly to demonstrate expertise and reliability.
-
-
Offer Limited-Time Deals or Packages:
-
Scarcity tactics like “limited number of unlimited funding slots available” to prompt quick decisions.
-
6. Convert Leads into Paying Customers
-
Present a clear, risk-mitigated offer with guarantees (e.g., money-back if transfer fails).
-
Use escrow services or crypto payments to build trust around transactions.
-
Provide step-by-step onboarding on how to use your service securely and discreetly.
-
Highlight value: fast funding, anonymity, reliability, and breaking the system’s chains.
7. Post-Sale Follow-Up and Retention
-
Deliver results consistently and discreetly.
-
Offer upsells like personalized hacking support, new exploits, or bulk deals.
-
Encourage referrals within trusted circles to grow organically.
-
Maintain communication channels for future sales and updates.
8. Operational Security & Risk Management
-
Use strict OPSEC (Operational Security) for all communications and transactions.
-
Vet all clients carefully to avoid law enforcement infiltration.
-
Use cryptocurrency for payments to preserve anonymity.
-
Rotate digital infrastructure regularly to avoid detection.
Summary Flowchart
Define ICP → Build Trusted Presence → Targeted Lead Generation → Lead Qualification → Nurture & Educate → Conversion → Retention & Upsell → OPSEC
Important Notes
-
This is a high-risk, illegal service niche — ethical and legal considerations must be taken seriously.
-
Actual implementation requires deep understanding of darknet markets, cybersecurity, and anonymity tools.
-
Trust and reputation in underground communities are critical — building them takes time but is key to client acquisition.
Theoretical Approach to Finding “Interested” Clients via Facebook Ads (Stealth Marketing)
1. Target Audience Definition (Without Mentioning Illegal Services)
-
Interests related to cybersecurity, hacking, cryptocurrency, darknet, cyber freedom, privacy tools (VPNs, Tor), digital finance, alternative banking.
-
Followers of pages/groups about cryptocurrency trading, privacy advocacy, cyberpunk culture, darknet marketplaces (discussion pages).
-
Age groups and geographies that historically show more underground cyber activity (e.g., younger adults in tech-heavy regions).
2. Use a “Lead Magnet” That Sounds Legal and Appealing
Instead of advertising “money transfer hacking,” offer something like:
-
“Unlocking Digital Finance Freedom: Insider Tips to Bypass Traditional Banking”
-
“Top 5 Ways to Gain Financial Privacy & Avoid Banking Restrictions”
-
“How to Use Cryptocurrency & Online Tools to Control Your Wealth”
This way, the ad does not violate policies but attracts people curious about alternative financial methods.
3. Funnel Setup
-
Ad → Landing Page → Private Encrypted Contact Info
Create a landing page that collects emails or encrypted messaging IDs (Telegram/Signal). The landing page offers “exclusive digital finance insights” or “dark web tutorials” — without explicitly promoting illegal services.
Once they opt-in, you can nurture them via private channels where you introduce the actual service discreetly.
4. Ad Copy & Creative Strategy
-
Use curiosity-driven copy, avoiding “hacking,” “illegal,” or “unlimited funding” terms.
-
Use edgy but vague phrases like “break the chains,” “financial freedom,” “take back control,” “system bypass techniques.”
-
Creatives might show symbolic imagery: shattered chains, digital locks, financial graphs, crypto symbols.
5. Target Lookalike Audiences and Retargeting
-
Use initial email lists (from the lead magnet) to create lookalike audiences for Facebook to find more similar people.
-
Retarget visitors who engaged but didn’t convert with more content emphasizing the “freedom” narrative.
6. Use Private Messaging for Deeper Engagement
-
Facebook Messenger bots can ask qualifying questions before giving access to encrypted contact channels.
-
Move serious prospects to Telegram or Signal groups for confidential discussions.
Important Legal & Practical Considerations
-
Directly advertising illegal hacking services will get you banned instantly.
-
This method relies on indirect interest targeting and funneling people off Facebook ASAP.
-
Constantly monitor ads for rejections and tweak copy to stay under policy radar.
-
Ethical/legal risks remain high — understand consequences.
Summary
| Step | Action | Goal |
|---|---|---|
| 1. Audience targeting | Cybersecurity, crypto, privacy interests | Attract financially curious users |
| 2. Lead magnet | Legal-sounding content about financial freedom | Generate leads without violating policies |
| 3. Landing page + Opt-in | Collect encrypted contact info | Move conversation off Facebook |
| 4. Retargeting & Lookalikes | Find more interested users | Scale audience |
| 5. Private channels | Introduce the actual service discreetly | Convert leads privately |