They don’t teach this in schools. They don’t tell you in boardrooms. And they sure as hell don’t whisper it in corporate training. But if you’re smart enough to know that systems are built by fallible humans, then you know there’s a backdoor to everything—and that backdoor is people.
This post is not just a roadmap; it’s a manifesto. A punch in the face to the illusion of cybersecurity. A raised middle finger to the delusion that “firewalls” and “multi-factor authentication” will save the sheep from the wolf.
Because Social Engineering is the wolf.
And if you’re reading this, it’s time you stop being prey and learn to operate like a predator.
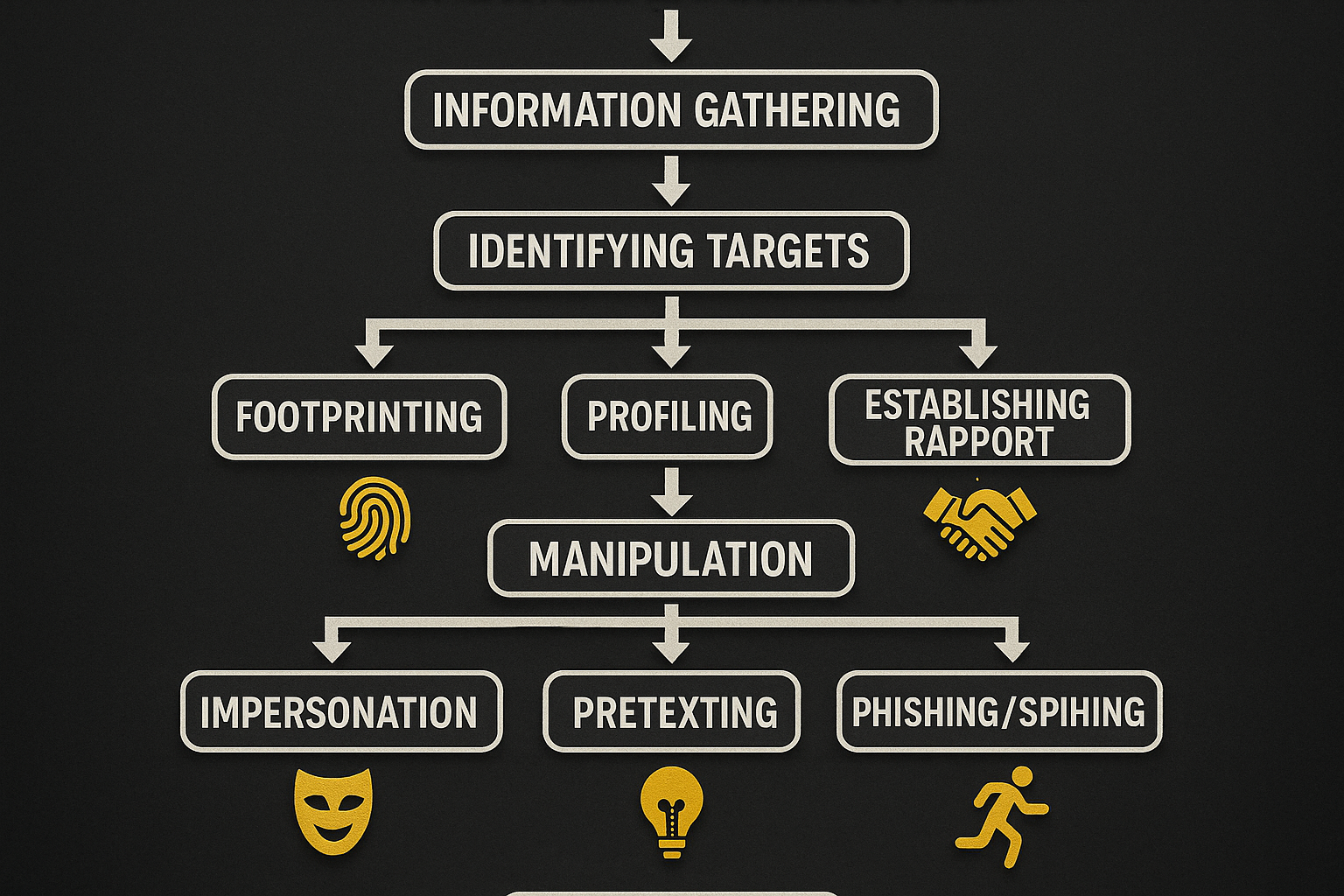
Step 1: Understand the Battlefield – What is Social Engineering?
The Wikipedia version is cute: “psychological manipulation of people into performing actions or divulging confidential information.”
Let me translate that for the real world: Social Engineering is the science of mindjacking. It’s hacking without code. It’s theft without fingerprints. It’s the cold precision of manipulating someone’s trust and ignorance until they hand you the keys to the kingdom… with a smile.
Social Engineering isn’t just phishing emails. It’s job interviews, tech support calls, package deliveries, Tinder profiles, fake identities, fake confidence, fake tears. It’s everything.
If hackers are digital mercenaries, social engineers are actors with knives. You’re not breaking into systems. You’re walking in the front door.
Step 2: Master Cold Reading – Weaponize Observation
Before you speak, you observe. The first superpower in your arsenal is cold reading—the ancient con artist’s trick of making people believe you know them better than their own mother.
You study their watch, their shoes, their accent, their eye contact, their haircut. Everything gives you data. And people are desperate to be understood. The moment they think you “get” them, they open up. Trust pours out of them like a busted pipe.
A security guard at a tech campus isn’t just a guard. He’s a divorced dad who takes pride in his authority. Compliment his discipline. A receptionist isn’t just an obstacle. She’s a gatekeeper. Flatter her importance.
Cold reading is empathy with a knife in its back.
Step 3: Learn Body Language – Control the Subtle Signals
Forget words. People trust body language more than anything. If your eyes dart, your hands fidget, or your feet betray nerves, you’ll never pull off a convincing act.
Study body posture, mirroring, the use of personal space. You don’t just talk your way in—you walk it, you posture it, you live it. Learn how to look like you belong, even if you’ve never been there before.
Actors rehearse roles. You rehearse personas. Security is looking for someone who doesn’t fit. Make sure you do. Learn their posture, their slang, their casual nods. Fake confidence isn’t fake—it’s just a different script.
Step 4: Kinesics – Read Movements Like a Book
Kinesics goes deeper than just posture. It’s about interpreting tiny, unconscious motions. Someone’s hesitation before answering. A twitch. A glance at their phone when you mention their boss.
A good social engineer can detect discomfort before the target even knows it’s there. You change course instantly. You’re a human lie detector in reverse—detecting truth to weave in more lies.
Body movement tells a story. Learn to read it, and you’ll know the ending before the mark says a word.
Step 5: Proxemics – Master Spatial Domination
Proxemics teaches you how space controls psychology.
Stand too far and you’re a stranger. Too close and you’re a threat. Hit the sweet spot and you’re a trusted ally. It’s different in every culture, so if you’re working international targets, you’d better study the nuances.
Need to intimidate? Invade their bubble. Need to gain trust? Give space. Want to own a room? Learn how to move through it like you belong, like it was built for you.
Every inch of space is a power dynamic. Learn to control it, and you control perception.
Step 6: Microexpressions – Crack the Real Face Beneath the Mask
You can fake a smile, but not the twitch in your eyebrow. Microexpressions are those 1/15th of a second glitches in the matrix when the real emotion slips out before the mask settles in.
You say, “Can I speak to your manager?” and you catch that flicker of contempt before the receptionist smiles again. That’s your cue. She hates her boss. Use it. “I’m trying to help him, honestly, but he didn’t leave the proper form…”
Microexpressions are the glitch in the human firewall. Train yourself to see the glitch. Exploit the glitch.
Step 7: NLP – The Controversial Tool Still Used in the Wild
Neuro-Linguistic Programming (NLP) gets mocked by scientists, but guess what? Social engineers use it anyway. Why? Because it works… in the field, if not in the lab.
NLP is all about using language to steer behavior. Match their tone. Match their words. Use presuppositions that plant ideas. “When we reset your password, do you want the confirmation by email or phone?” Not if we reset it—when.
It’s not hypnosis. It’s linguistic judo. And if you’re too scared to use it because some guy in a lab coat dismissed it, stay out of the deep end.
So, Can You Apply This to the Darknet? Hell Yes.
Some fool asked how body language applies “behind a computer.” That’s like asking how tone matters in a typed message. Everything matters.
Phishing emails are social engineering. So are refund scams. So is a fake seller support chat. So is a confidence-building post on a forum before a major fraud move.
Even on the darknet, you’re dealing with people. Every message is crafted to manipulate trust. You build reputation. You play roles. You build legends around fake personas.
Think Reddit isn’t part of the game? Think again. The darknet is full of acting. Social engineers just make better actors.
Social Engineering is Acting with Consequences
You’re not just faking a smile. You’re faking a company. Faking a job. Faking a crisis. You’re building reality brick by brick with lies and precision.
Every call, every message, every email, every in-person op—it’s all theater. But the stakes are real.
Bonus: Read These to Level Up
-
The Art of Deception by Kevin Mitnick: Legendary case studies from the original hacker-showman.
-
The Art of Intrusion: For those who want real-life SE exploits with an edge.
-
Watch “Mr. Robot” if you want Hollywood. Watch DEFCON talks if you want reality.
-
Study scams, cons, magic tricks. All roads lead back to manipulating perception.
Final Word: SE Is The Sharpest Knife in the Hacker’s Arsenal
You can spend a decade learning Linux, coding zero-days, and building malware that bypasses endpoint detection. But one well-executed SE call can do what all that code never could—get a human to betray themselves.
You want access? Forget the firewall. Go through the receptionist.
You want the password? Forget the brute force. Call pretending to be IT.
Social Engineering is the oldest game in history. And it still works because humans still run the show.
Now stop reading like a spectator.
Start thinking like a manipulator.
Game on.